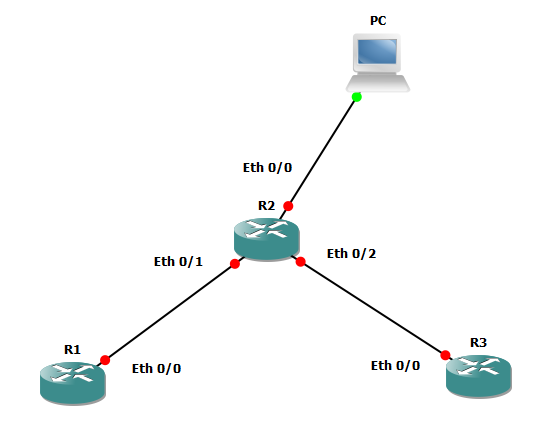
Packet analysis is a crucial skill for application level troubleshooting. Primary tool is Wireshark and following are some commands which will often come in handy to filter the interested traffic.
Additional Notes:-
Filtering Conditions
These are the filtering criteria to be matched and displayed. You just need to type the line in filter tool bar.
Logical Operators
You can just type the name of the operator in English or you can use the logical symbols like you do in programming to make a logical filter which will display the logical truth result of 2 or more conditions.
Using above commands, conditions & operators you can write complex statements like the following to filter packets in a capture.
Ex:- !(ip.flags == 0x40) && ip.addr==10.227.54.142
Additional Notes:-
If you want to filter packets by a protocol name, you just need to type the protocol name
Ex:- 'dns' will display all the DNS packets
Ex:- 'http' will display all the http packets
If you want to find TCP packets with ACK flag set, you should use 'tcp.flags.ack == 1'
If you want the TCP packets with acknoledgement number equal to 1 'tcp.ack == 1'
Use 'frames.len > 1514' will display the jumbo frames.